Question 13 : Which Of The Following Is Not Considered A Denial-of-service Attack?
Security
References:
- Abraham Silberschatz, Greg Gagne, and Peter Baer Galvin, "Operating Organisation Concepts, Seventh Edition ", Chapter 15
Notation:
- This is a brief one-chapter introduction to a very large and of import topic. Students interested in the topic of Computer Security may want to consider following this course up with CS 487- Building Trustworthy Computer Systems, CS 587 Estimator Systems Security, or CS 588 Security and Privacy in Networked and Distributed Systems.
xv.1 The Security Problem
- Chapter 14 ( Protection ) dealt with protecting files and other resources from accidental misuse by cooperating users sharing a system, more often than not using the computer for normal purposes.
- This affiliate ( Security ) deals with protecting systems from deliberate attacks, either internal or external, from individuals intentionally attempting to steal information, impairment data, or otherwise deliberately wreak havoc in some manner.
- Some of the nigh common types of violations include:
- Breach of Confidentiality - Theft of private or confidential information, such as credit-card numbers, merchandise secrets, patents, secret formulas, manufacturing procedures, medical information, financial information, etc.
- Breach of Integrity - Unauthorized modification of data, which may accept serious indirect consequences. For example a popular game or other program's source lawmaking could be modified to open up security holes on users systems earlier being released to the public.
- Breach of Availability - Unauthorized destruction of data, ofttimes only for the "fun" of causing havoc and for bragging rites. Vandalism of web sites is a common grade of this violation.
- Theft of Service - Unauthorized use of resource, such every bit theft of CPU cycles, installation of daemons running an unauthorized file server, or tapping into the target's telephone or networking services.
- Deprival of Service, DOS - Preventing legitimate users from using the system, oftentimes by overloading and overwhelming the system with an backlog of requests for service.
- Ane common assail is masquerading, in which the assaulter pretends to be a trusted tertiary political party. A variation of this is the man-in-the-center, in which the attacker masquerades every bit both ends of the conversation to ii targets.
- A replay assault involves repeating a valid manual. Sometimes this tin exist the entire attack, ( such equally repeating a request for a money transfer ), or other times the content of the original message is replaced with malicious content.
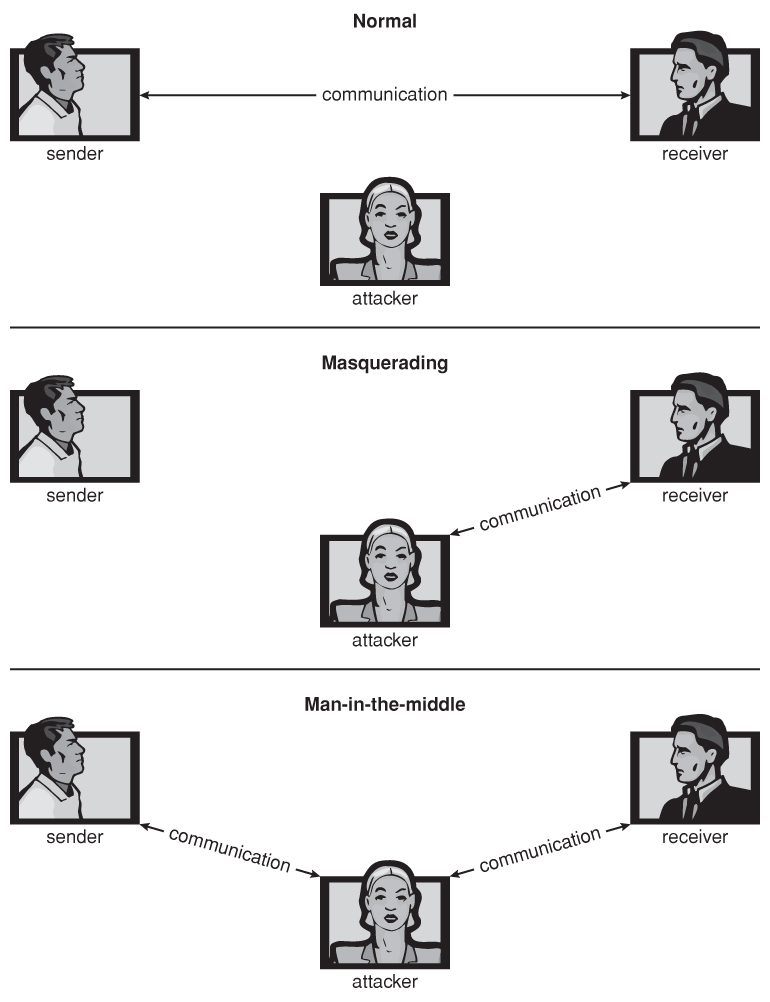
Figure 15.1 - Standard security attacks.
- At that place are four levels at which a system must be protected:
- Concrete - The easiest way to steal data is to pocket the backup tapes. Also, access to the root panel will often requite the user special privileges, such as rebooting the system every bit root from removable media. Even general access to terminals in a figurer room offers some opportunities for an attacker, although today'south modern high-speed networking environment provides more and more than opportunities for remote attacks.
- Man - There is some concern that the humans who are allowed access to a system exist trustworthy, and that they cannot be coerced into breaching security. However more and more attacks today are made via social engineering, which basically means fooling trustworthy people into accidentally breaching security.
- Phishing involves sending an innocent-looking east-postal service or web site designed to fool people into revealing confidential data. Eastward.thousand. spam e-mails pretending to exist from east-Bay, PayPal, or any of a number of banks or credit-card companies.
- Dumpster Diving involves searching the trash or other locations for passwords that are written down. ( Annotation: Passwords that are too hard to call back, or which must be changed often are more than likely to exist written down somewhere close to the user's station. )
- Countersign Swell involves divining users passwords, either by watching them type in their passwords, knowing something almost them like their pet'due south names, or simply trying all words in mutual dictionaries. ( Notation: "Good" passwords should involve a minimum number of characters, include non-alphabetical characters, and not appear in any lexicon ( in any linguistic communication ), and should exist changed frequently. Annotation besides that it is proper etiquette to await abroad from the keyboard while someone else is entering their password. )
- Operating Organization - The Bone must protect itself from security breaches, such as delinquent processes ( deprival of service ), memory-admission violations, stack overflow violations, the launching of programs with excessive privileges, and many others.
- Network - As network communications become ever more important and pervasive in modernistic computing environments, information technology becomes always more than important to protect this area of the arrangement. ( Both protecting the network itself from attack, and protecting the local system from attacks coming in through the network. ) This is a growing area of business concern equally wireless communications and portable devices become more than and more prevalent.
xv.2 Program Threats
- There are many common threats to mod systems. Only a few are discussed here.
15.two.ane Trojan Equus caballus
- A Trojan Horse is a plan that secretly performs some maliciousness in add-on to its visible actions.
- Some Trojan horses are deliberately written every bit such, and others are the consequence of legitimate programs that have go infected with viruses, ( see below. )
- 1 dangerous opening for Trojan horses is long search paths, and in particular paths which include the current directory ( "." ) as part of the path. If a dangerous plan having the aforementioned proper noun as a legitimate program ( or a common mis-spelling, such as "sl" instead of "ls" ) is placed anywhere on the path, then an unsuspecting user may be fooled into running the incorrect program past error.
- Another archetype Trojan Equus caballus is a login emulator, which records a users account proper noun and password, problems a "countersign incorrect" message, and and then logs off the organisation. The user and so tries again ( with a proper login prompt ), logs in successfully, and doesn't realize that their information has been stolen.
- ( Special Note to UIC students: Beware that someone has registered the domain name of uic.European union ( without the "D" ), and is running an ssh server which will accept requests to whatsoever machine in the domain, and gladly accept your login and password information, without, of course, actually logging you lot in. Access to this site is blocked from campus, only you are on your ain off campus. )
- Two solutions to Trojan Horses are to take the system impress usage statistics on logouts, and to require the typing of non-trappable key sequences such as Control-Alt-Delete in gild to log in. ( This is why modern Windows systems crave the Control-Alt-Delete sequence to commence logging in, which cannot be emulated or caught by ordinary programs. I.due east. that key sequence e'er transfers control over to the operating system. )
- Spyware is a version of a Trojan Horse that is frequently included in "complimentary" software downloaded off the Cyberspace. Spyware programs generate pop-up browser windows, and may likewise accumulate information well-nigh the user and deliver it to some key site. ( This is an example of covert channels, in which clandestine communications occur. ) Another common task of spyware is to ship out spam e-mail messages, which and so purportedly come up from the infected user.
xv.two.2 Trap Door
- A Trap Door is when a designer or a programmer ( or hacker ) deliberately inserts a security hole that they tin can use afterwards to access the organisation.
- Because of the possibility of trap doors, once a arrangement has been in an untrustworthy state, that system can never be trusted again. Even the backup tapes may contain a copy of some cleverly hidden back door.
- A clever trap door could be inserted into a compiler, then that whatsoever programs compiled with that compiler would incorporate a security hole. This is especially dangerous, because inspection of the code beingness compiled would not reveal whatsoever bug.
fifteen.2.3 Logic Bomb
- A Logic Bomb is code that is not designed to crusade havoc all the time, but just when a certain set of circumstances occurs, such equally when a particular date or time is reached or some other noticeable upshot.
- A classic case is the Dead-Human Switch , which is designed to check whether a sure person ( eastward.g. the author ) is logging in every day, and if they don't log in for a long time ( presumably because they've been fired ), then the logic flop goes off and either opens upwardly security holes or causes other issues.
15.2.4 Stack and Buffer Overflow
- This is a classic method of attack, which exploits bugs in system code that allows buffers to overflow. Consider what happens in the following code, for example, if argv[ one ] exceeds 256 characters:
- The strcpy control will overflow the buffer, overwriting side by side areas of memory.
- ( The problem could be avoided using str n cpy, with a limit of 255 characters copied plus room for the null byte. )
#include#define BUFFER_SIZE 256 int main( int argc, char * argv[ ] ) { char buffer[ BUFFER_SIZE ]; if( argc < 2 ) return -1; else { strcpy( buffer, argv[ ane ] ); return 0; } } Figure 15.ii - C program with buffer-overflow condition.
- So how does flood the buffer cause a security alienation? Well the first step is to understand the structure of the stack in retention:
- The "bottom" of the stack is actually at a high retentivity address, and the stack grows towards lower addresses.
- Nonetheless the address of an array is the lowest accost of the array, and higher array elements extend to higher addresses. ( I.e. an array "grows" towards the bottom of the stack.
- In particular, writing past the top of an assortment, as occurs when a buffer overflows with too much input data, can eventually overwrite the return address, effectively changing where the program jumps to when it returns.
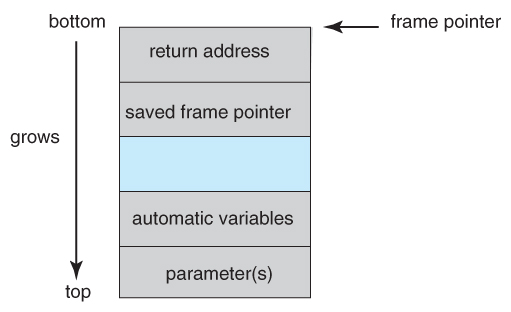
Figure xv.three - The layout for a typical stack frame.
- At present that nosotros know how to change where the program returns to past overflowing the buffer, the 2nd step is to insert some nefarious code, and then get the program to jump to our inserted code.
- Our only opportunity to enter code is via the input into the buffer, which means in that location isn't room for very much. Ane of the simplest and most obvious approaches is to insert the code for "exec( /bin/sh )". To do this requires compiling a plan that contains this pedagogy, and and then using an assembler or debugging tool to extract the minimum extent that includes the necessary instructions.
- The bad code is then padded with as many extra bytes equally are needed to overflow the buffer to the correct extent, and the address of the buffer inserted into the return address location. ( Note, even so, that neither the bad code or the padding can contain zippo bytes, which would finish the strcpy. )
- The resulting block of information is provided as "input", copied into the buffer past the original plan, and and so the return statement causes control to jump to the location of the buffer and starting time executing the lawmaking to launch a crush.
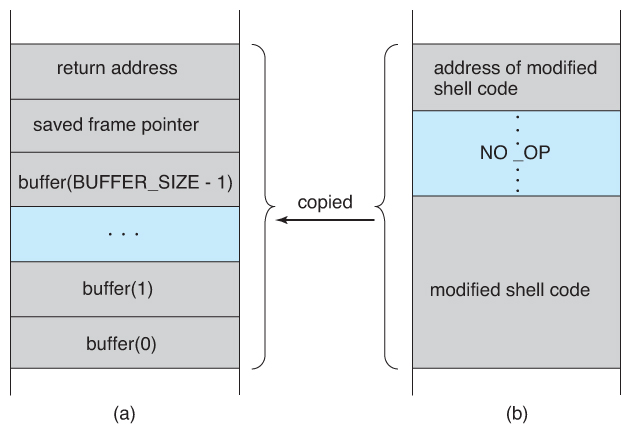
Figure 15.four - Hypothetical stack frame for Figure 15.two, (a) earlier and (b) after.
- Unfortunately famous hacks such as the buffer overflow attack are well published and well known, and information technology doesn't take a lot of skill to follow the instructions and start attacking lots of systems until the law of averages somewhen works out. ( Script Kiddies are those hackers with only rudimentary skills of their ain but the ability to copy the efforts of others. )
- Fortunately modern hardware now includes a bit in the page tables to mark sure pages every bit non-executable. In this case the buffer-overflow attack would work up to a point, simply as shortly as information technology "returns" to an address in the data infinite and tries executing statements there, an exception would exist thrown crashing the programme.
- ( More details about stack-overflow attacks are available on-line from http://world wide web.insecure.org/stf/smashstack.txt )
fifteen.2.5 Viruses
- A virus is a fragment of lawmaking embedded in an otherwise legitimate program, designed to replicate itself ( by infecting other programs ), and ( eventually ) wreaking havoc.
- Viruses are more likely to infect PCs than UNIX or other multi-user systems, because programs in the latter systems have limited authority to modify other programs or to access critical system structures ( such every bit the boot block. )
- Viruses are delivered to systems in a virus dropper, normally some form of a Trojan Equus caballus, and usually via e-mail or unsafe downloads.
- Viruses take many forms ( see beneath. ) Figure 15.v shows typical performance of a boot sector virus:
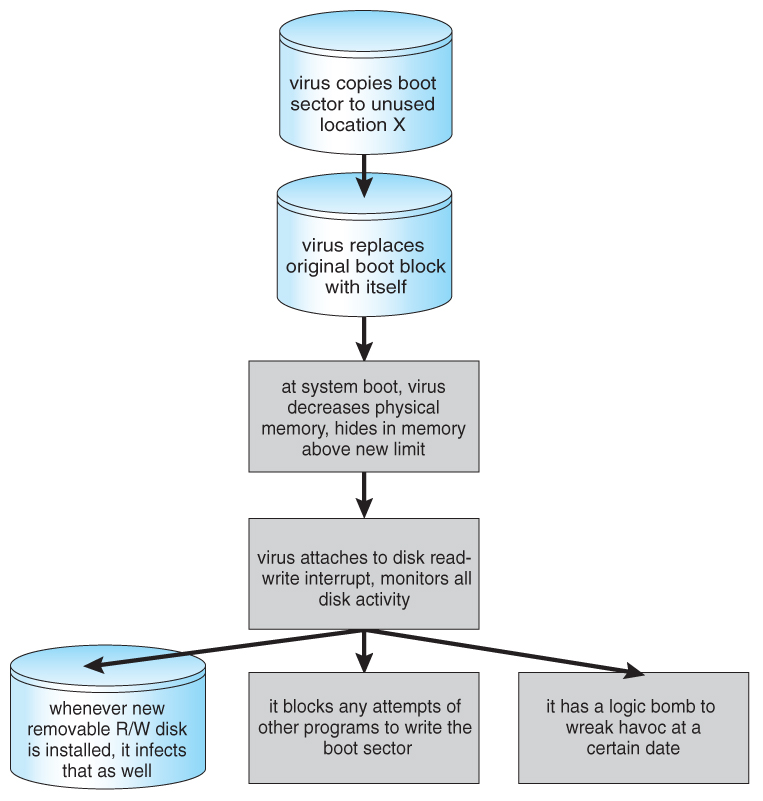
Figure 15.5 - A boot-sector computer virus.
- Some of the forms of viruses include:
- File - A file virus attaches itself to an executable file, causing it to run the virus code kickoff and then leap to the start of the original plan. These viruses are termed parasitic, because they do not leave any new files on the system, and the original program is however fully functional.
- Boot - A boot virus occupies the boot sector, and runs before the OS is loaded. These are also known as retentiveness viruses , because in operation they reside in memory, and do not appear in the file organisation.
- Macro - These viruses exist as a macro ( script ) that are run automatically by certain macro-capable programs such as MS Discussion or Excel. These viruses tin exist in word processing documents or spreadsheet files.
- Source code viruses wait for source code and infect information technology in lodge to spread.
- Polymorphic viruses change every time they spread - Not their underlying functionality, only only their signature, by which virus checkers recognize them.
- Encrypted viruses travel in encrypted form to escape detection. In do they are cocky-decrypting, which and then allows them to infect other files.
- Stealth viruses try to avoid detection by modifying parts of the organisation that could be used to detect it. For case the read( ) system call could exist modified so that if an infected file is read the infected part gets skipped and the reader would see the original unadulterated file.
- Tunneling viruses endeavor to avoid detection by inserting themselves into the interrupt handler chain, or into device drivers.
- Multipartite viruses assault multiple parts of the organization, such as files, kick sector, and memory.
- Armored viruses are coded to make them difficult for anti-virus researchers to decode and understand. In addition many files associated with viruses are subconscious, protected, or given innocuous looking names such equally "...".
- In 2004 a virus exploited three bugs in Microsoft products to infect hundreds of Windows servers ( including many trusted sites ) running Microsoft Cyberspace Information Server, which in turn infected whatsoever Microsoft Internet Explorer spider web browser that visited whatsoever of the infected server sites. One of the back-door programs it installed was a keystroke logger, which records users keystrokes, including passwords and other sensitive data.
- There is some debate in the computing community as to whether a monoculture, in which near all systems run the same hardware, operating arrangement, and applications, increases the threat of viruses and the potential for impairment caused by them.
fifteen.three Organization and Network Threats
- Most of the threats described to a higher place are termed program threats , because they attack specific programs or are carried and distributed in programs. The threats in this section attack the operating arrangement or the network itself, or leverage those systems to launch their attacks.
15.three.1 Worms
- A worm is a process that uses the fork / spawn process to brand copies of itself in club to wreak havoc on a arrangement. Worms consume arrangement resources, often blocking out other, legitimate processes. Worms that propagate over networks tin can exist peculiarly problematic, as they tin can tie up vast amounts of network resource and bring downwardly big-scale systems.
- 1 of the most well-known worms was launched past Robert Morris, a graduate student at Cornell, in November 1988. Targeting Sun and VAX computers running BSD UNIX version iv, the worm spanned the Cyberspace in a matter of a few hours, and consumed plenty resources to bring down many systems.
- This worm consisted of two parts:
- A small program called a grappling hook, which was deposited on the target system through one of three vulnerabilities, and
- The main worm program, which was transferred onto the target organisation and launched by the grappling hook program.
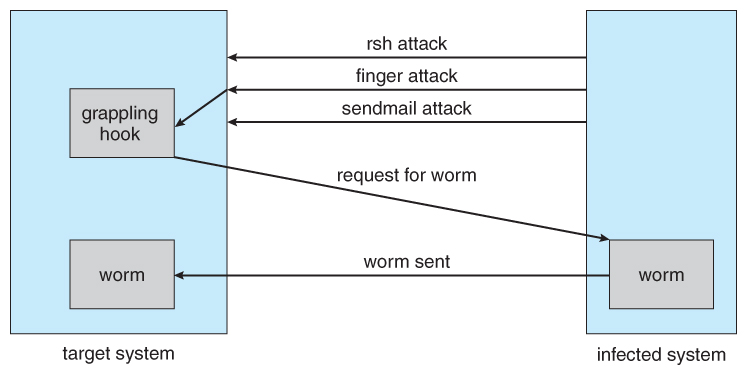
Effigy 15.6 - The Morris Internet worm.
- The three vulnerabilities exploited by the Morris Cyberspace worm were as follows:
- rsh ( remote shell ) is a utility that was in common use at that time for accessing remote systems without having to provide a countersign. If a user had an account on two different computers ( with the same account name on both systems ), then the system could be configured to allow that user to remotely connect from 1 organization to the other without having to provide a countersign. Many systems were configured and so that whatever user ( except root ) on system A could access the same account on system B without providing a password.
- finger is a utility that allows one to remotely query a user database, to find the truthful name and other information for a given account proper noun on a given system. For example "finger joeUser@somemachine.edu" would admission the finger daemon at somemachine.edu and return information regarding joeUser. Unfortunately the finger daemon ( which ran with system privileges ) had the buffer overflow trouble, so by sending a special 536-character user name the worm was able to fork a shell on the remote system running with root privileges.
- sendmail is a routine for sending and forwarding mail that also included a debugging selection for verifying and testing the organization. The debug feature was convenient for administrators, and was oft left turned on. The Morris worm exploited the debugger to mail and execute a copy of the grappling hook program on the remote system.
- Once in identify, the worm undertook systematic attacks to find user passwords:
- First it would bank check for accounts for which the business relationship name and the password were the aforementioned, such as "guest", "guest".
- And then it would effort an internal dictionary of 432 favorite password choices. ( I'yard sure "countersign", "laissez passer", and bare passwords were all on the list. )
- Finally it would endeavour every give-and-take in the standard UNIX on-line lexicon to try and pause into user accounts.
- Once it had gotten access to one or more user accounts, then it would effort to use those accounts to rsh to other systems, and continue the procedure.
- With each new admission the worm would bank check for already running copies of itself, and vi out of vii times if it found one it would stop. ( The 7th was to preclude the worm from existence stopped by fake copies. )
- Fortunately the same rapid network connectivity that allowed the worm to propagate so speedily also rapidly led to its demise - Within 24 hours remedies for stopping the worm propagated through the Net from administrator to administrator, and the worm was quickly shut down.
- There is some debate nigh whether Mr. Morris's actions were a harmless prank or research projection that got out of paw or a deliberate and malicious set on on the Cyberspace. However the court arrangement convicted him, and penalized him heavy fines and courtroom costs.
- At that place have since been many other worm attacks, including the W32.Sobig.F@mm attack which infected hundreds of thousands of computers and an estimated i in 17 e-mails in Baronial 2003. This worm made detection difficult by varying the subject line of the infection-carrying post bulletin, including "Give thanks Y'all!", "Your details", and "Re: Canonical".
15.3.2 Port Scanning
- Port Scanning is technically non an attack, but rather a search for vulnerabilities to assault. The basic idea is to systematically try to connect to every known ( or common or possible ) network port on some remote automobile, and to attempt to make contact. Once it is adamant that a particular computer is listening to a particular port, then the next stride is to decide what daemon is listening, and whether or non it is a version containing a known security flaw that can exist exploited.
- Considering port scanning is hands detected and traced, information technology is usually launched from zombie systems, i.e. previously hacked systems that are being used without the knowledge or permission of their rightful owner. For this reason it is important to protect "innocuous" systems and accounts as well as those that contain sensitive information or special privileges.
- There are also port scanners available that administrators can utilize to check their own systems, which report any weaknesses plant but which do not exploit the weaknesses or cause any issues. Two such systems are nmap ( http://www.insecure.org/nmap ) and nessus ( http://www.nessus.org ). The former identifies what OS is institute, what firewalls are in identify, and what services are listening to what ports. The latter also contains a database of known security holes, and identifies any that it finds.
15.3.3 Deprival of Service
- Denial of Service ( DOS ) attacks do not endeavor to actually access or harm systems, simply merely to clog them up so badly that they cannot be used for any useful work. Tight loops that repeatedly request arrangement services are an obvious form of this set on.
- DOS attacks can besides involve social engineering science, such as the Internet chain letters that say "transport this immediately to 10 of your friends, and then get to a sure URL", which clogs upwards not only the Internet mail system merely too the spider web server to which anybody is directed. ( Notation: Sending a "reply all" to such a bulletin notifying everyone that it was just a hoax as well clogs upwards the Internet mail service, just equally finer as if you had forwarded the matter. )
- Security systems that lock accounts later on a certain number of failed login attempts are subject to DOS attacks which repeatedly attempt logins to all accounts with invalid passwords strictly in club to lock upward all accounts.
- Sometimes DOS is not the event of deliberate maliciousness. Consider for example:
- A web site that sees a huge book of hits as a effect of a successful advertising campaign.
- CNN.com occasionally gets overwhelmed on big news days, such every bit Sept eleven, 2001.
- CS students given their first programming assignment involving fork( ) frequently rapidly make full process tables or otherwise completely eat system resources. :-)
- ( Delight utilize ipcs and ipcrm when working on the inter-process communications assignment ! )
15.4 Cryptography as a Security Tool
- Within a given estimator the transmittal of messages is safe, reliable and secure, because the OS knows exactly where each 1 is coming from and where it is going.
- On a network, however, things aren't and so straightforward - A rogue computer ( or e-mail sender ) may spoof their identity, and approachable packets are delivered to a lot of other computers besides their ( intended ) terminal destination, which brings upward two big questions of security:
- Trust - How can the system be certain that the messages received are really from the source that they say they are, and tin can that source be trusted?
- Confidentiality - How can one ensure that the messages one is sending are received only past the intended recipient?
- Cryptography tin can assist with both of these problems, through a system of secrets and keys. In the one-time instance, the key is held by the sender, then that the recipient knows that only the authentic author could have sent the message; In the latter, the key is held by the recipient, so that just the intended recipient can receive the message accurately.
- Keys are designed so that they cannot be divined from any public information, and must be guarded carefully. ( Asymmetric encryption involve both a public and a private key. )
15.four.1 Encryption
- The bones idea of encryption is to encode a message so that only the desired recipient can decode and read it. Encryption has been around since before the days of Caesar, and is an entire subject field in itself. Only some of the more meaning figurer encryption schemes will be covered here.
- The basic procedure of encryption is shown in Figure 15.vii, and will class the footing of most of our discussion on encryption. The steps in the procedure and some of the key terminology are as follows:
- The sender commencement creates a message, m in plaintext.
- The message is so entered into an encryption algorithm, E, along with the encryption key, Ke.
- The encryption algorithm generates the ciphertext, c, = E(Ke)(grand). For any key g, E(k) is an algorithm for generating ciphertext from a message, and both Due east and E(yard) should be efficiently computable functions.
- The ciphertext tin then be sent over an unsecure network, where it may be received by attackers.
- The recipient enters the ciphertext into a decryption algorithm, D, forth with the decryption fundamental, Kd.
- The decryption algorithm re-generates the plaintext message, grand, = D(Kd)(c). For any fundamental k, D(k) is an algorithm for generating a clear text bulletin from a ciphertext, and both D and D(g) should exist efficiently computable functions.
- The algorithms described here must accept this important holding: Given a ciphertext c, a computer tin can merely compute a message yard such that c = Eastward(k)(g) if it possesses D(k). ( In other words, the messages can't be decoded unless you lot accept the decryption algorithm and the decryption key. )
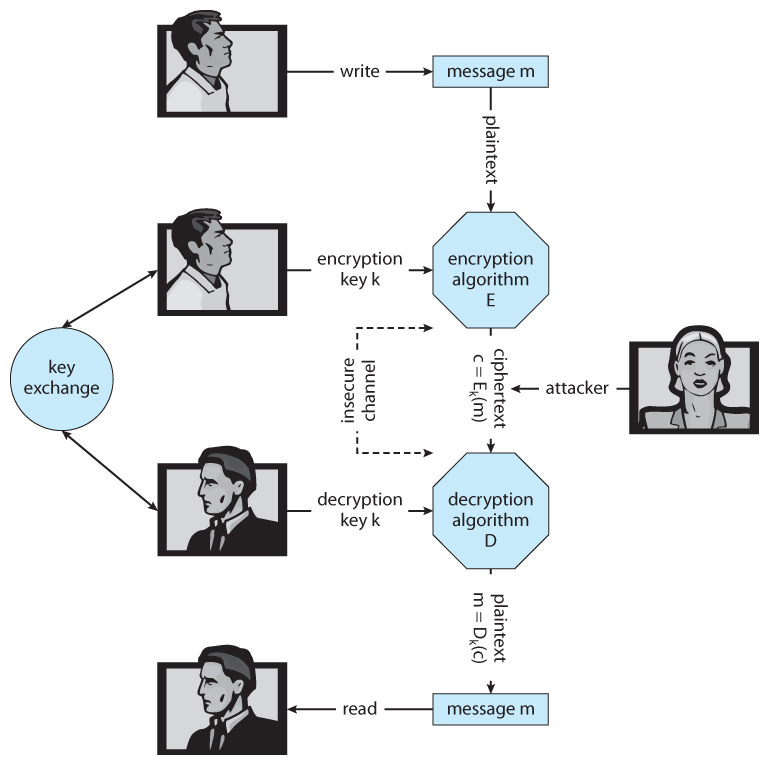
Effigy 15.vii - A secure communication over an insecure medium.15.4.1.1 Symmetric Encryption
- With symmetric encryption the aforementioned key is used for both encryption and decryption, and must exist safely guarded. In that location are a number of well-known symmetric encryption algorithms that have been used for figurer security:
- The Data-Encryption Standard, DES, developed by the National Establish of Standards, NIST, has been a standard civilian encryption standard for over 20 years. Messages are broken downwards into 64-bit chunks, each of which are encrypted using a 56-bit key through a series of substitutions and transformations. Some of the transformations are hidden ( black boxes ), and are classified by the U.Southward. government.
- DES is known as a block nothing, because it works on blocks of data at a time. Unfortunately this is a vulnerability if the same key is used for an extended corporeality of data. Therefore an enhancement is to not just encrypt each block, but also to XOR it with the previous block, in a technique known as cipher-block chaining.
- As modern computers go faster and faster, the security of DES has decreased, to where it is now considered insecure because its keys tin can be exhaustively searched within a reasonable corporeality of reckoner time. An enhancement chosen triple DES encrypts the data three times using three dissever keys ( really two encryptions and one decryption ) for an effective key length of 168 $.25. Triple DES is in widespread utilize today.
- The Advanced Encryption Standard, AES, developed by NIST in 2001 to replace DES uses cardinal lengths of 128, 192, or 256 $.25, and encrypts in blocks of 128 bits using 10 to 14 rounds of transformations on a matrix formed from the cake.
- The twofish algorithm, uses variable central lengths up to 256 bits and works on 128 scrap blocks.
- RC5 can vary in central length, block size, and the number of transformations, and runs on a wide variety of CPUs using simply basic computations.
- RC4 is a stream cipher, meaning information technology acts on a stream of data rather than blocks. The key is used to seed a pseudo-random number generator, which generates a keystream of keys. RC4 is used in WEP, merely has been institute to be breakable in a reasonable corporeality of computer fourth dimension.
xv.4.1.2 Asymmetric Encryption
- With asymmetric encryption, the decryption key, Kd, is not the aforementioned as the encryption key, Ke, and more importantly cannot exist derived from it, which means the encryption key can be made publicly available, and only the decryption key needs to be kept secret. ( or vice-versa, depending on the application. )
- One of the virtually widely used disproportionate encryption algorithms is RSA, named subsequently its developers - Rivest, Shamir, and Adleman.
- RSA is based on ii large prime number numbers, p and q, ( on the order of 512 $.25 each ), and their product Northward.
- Ke and Kd must satisfy the relationship:
( Ke * Kd ) % [ ( p - 1 ) * ( q - i ) ] = = 1- The encryption algorithm is:
c = E(Ke)(1000) = m^Ke % Northward- The decryption algorithm is:
m = D(Kd)(c) = c^Kd % Northward- An example using minor numbers:
- p = vii
- q = 13
- N = 7 * 13 = 91
- ( p - 1 ) * ( q - 1 ) = 6 * 12 = 72
- Select Ke < 72 and relatively prime to 72, say 5
- Now select Kd, such that ( Ke * Kd ) % 72 = = ane, say 29
- The public fundamental is now ( 5, 91 ) and the private primal is ( 29, 91 )
- Let the message, one thousand = 42
- Encrypt: c = 42^five % 91 = 35
- Decrypt: m = 35^29 % 91 = 42
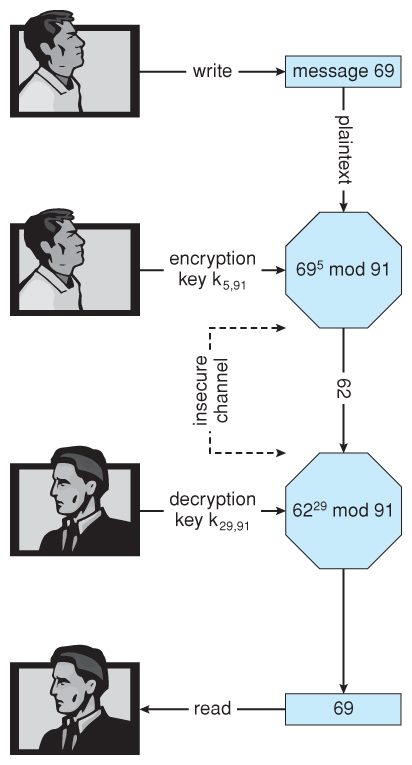
Effigy fifteen.8 - Encryption and decryption using RSA disproportionate cryptography
- Notation that asymmetric encryption is much more computationally expensive than symmetric encryption, and as such it is not usually used for large transmissions. Asymmetric encryption is suitable for modest messages, authentication, and key distribution, as covered in the following sections.
fifteen.4.1.3 Authentication
- Authentication involves verifying the identity of the entity who transmitted a message.
- For case, if D(Kd)(c) produces a valid message, then we know the sender was in possession of E(Ke).
- This form of authentication tin can also be used to verify that a bulletin has not been modified
- Authentication revolves around two functions, used for signatures ( or signing ), and verification:
- A signing function, S(Ks) that produces an authenticator, A, from any given message m.
- A Verification function, Five(Kv,m,A) that produces a value of "truthful" if A was created from 1000, and "faux" otherwise.
- Plainly S and V must both be computationally efficient.
- More importantly, information technology must not exist possible to generate a valid authenticator, A, without having possession of S(Ks).
- Furthermore, information technology must not be possible to divine South(Ks) from the combination of ( m and A ), since both are sent visibly beyond networks.
- Understanding authenticators begins with an understanding of hash functions, which is the first step:
- Hash functions, H(m) generate a small stock-still-size block of information known equally a message digest, or hash value from whatever given input data.
- For authentication purposes, the hash function must exist collision resistant on grand. That is it should not be reasonably possible to find an alternate message m' such that H(grand') = H(m).
- Popular hash functions are MD5, which generates a 128-fleck bulletin assimilate, and SHA-1, which generates a 160-bit digest.
- Message digests are useful for detecting ( accidentally ) changed letters, just are not useful every bit authenticators, because if the hash part is known, then someone could hands alter the message and and then generate a new hash value for the modified message. Therefore authenticators accept things one step further by encrypting the message assimilate.
- A message-authentication code, MAC, uses symmetric encryption and decryption of the message digest, which means that anyone capable of verifying an incoming bulletin could also generate a new message.
- An disproportionate arroyo is the digital-signature algorithm, which produces authenticators chosen digital signatures. In this case Ks and Kv are divide, Kv is the public central, and it is not practical to determine Southward(Ks) from public data. In practice the sender of a message signs it ( produces a digital signature using S(Ks) ), and the receiver uses Five(Kv) to verify that it did indeed come up from a trusted source, and that it has not been modified.
- There are three good reasons for having separate algorithms for encryption of messages and authentication of messages:
- Authentication algorithms typically crave fewer calculations, making verification a faster functioning than encryption.
- Authenticators are well-nigh always smaller than the messages, improving infinite efficiency. (?)
- Sometimes we want authentication only, and non confidentiality, such as when a vendor issues a new software patch.
- Another use of hallmark is non-repudiation, in which a person filling out an electronic form cannot deny that they were the ones who did so.
xv.four.1.4 Key Distribution
- Key distribution with symmetric cryptography is a major problem, because all keys must be kept secret, and they plain tin can't be transmitted over unsecure channels. I option is to transport them out-of-band, say via paper or a confidential chat.
- Another problem with symmetric keys, is that a separate fundamental must exist maintained and used for each correspondent with whom one wishes to exchange confidential information.
- Asymmetric encryption solves some of these problems, because the public primal tin can be freely transmitted through whatever aqueduct, and the private key doesn't demand to be transmitted anywhere. Recipients only need to maintain one private key for all incoming messages, though senders must maintain a separate public key for each recipient to which they might wish to send a message. Fortunately the public keys are not confidential, so this cardinal-ring tin can be hands stored and managed.
- Unfortunately in that location are still some security concerns regarding the public keys used in asymmetric encryption. Consider for example the following man-in-the-middle assail involving phony public keys:
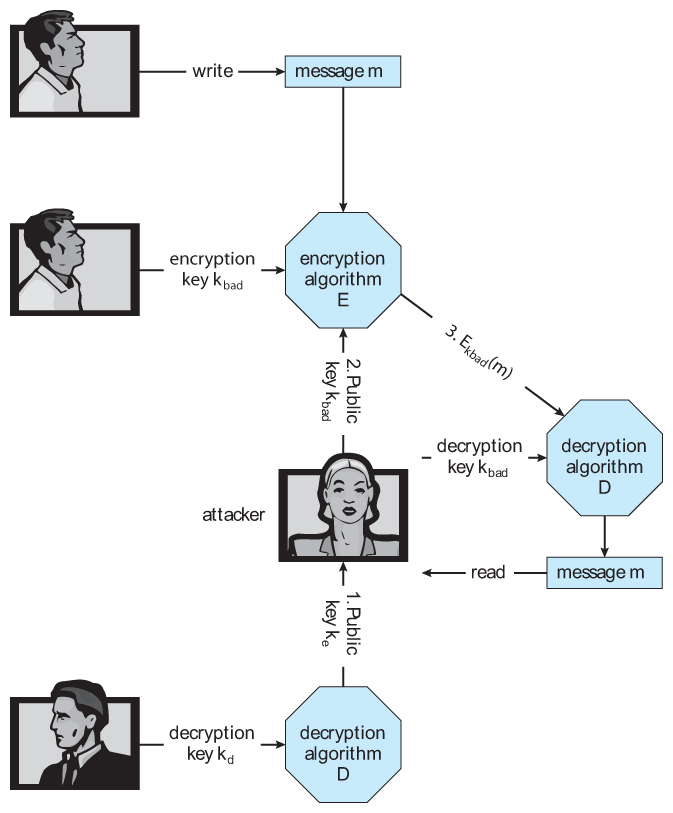
Effigy xv.9 - A man-in-the-eye attack on asymmetric cryptography.
- I solution to the above problem involves digital certificates, which are public keys that have been digitally signed by a trusted third party. Only wait a minute - How do we trust that third political party, and how practise we know they are really who they say they are? Certain document authorities have their public keys included within web browsers and other certificate consumers before they are distributed. These certificate authorities tin can and then vouch for other trusted entities and so on in a web of trust, as explained more than fully in section 15.iv.3.
fifteen.4.2 Implementation of Cryptography
- Network communications are implemented in multiple layers - Physical, Data Link, Network, Send, and Application beingness the most common breakdown.
- Encryption and security tin can be implemented at any layer in the stack, with pros and cons to each choice:
- Because packets at lower levels contain the contents of higher layers, encryption at lower layers automatically encrypts college layer information at the aforementioned fourth dimension.
- However security and potency may exist important to college levels contained of the underlying send mechanism or route taken.
- At the network layer the most common standard is IPSec, a secure form of the IP layer, which is used to set up Virtual Private Networks, VPNs.
- At the send layer the most common implementation is SSL, described below.
fifteen.four.iii An Instance: SSL
- SSL ( Secure Sockets Layer ) 3.0 was first developed past Netscape, and has now evolved into the industry-standard TLS protocol. It is used past web browsers to communicate deeply with web servers, making information technology maybe the most widely used security protocol on the Internet today.
- SSL is quite complex with many variations, just a simple case of which is shown hither.
- The middle of SSL is session keys , which are used once for symmetric encryption and then discarded, requiring the generation of new keys for each new session. The big challenge is how to safely create such keys while avoiding man-in-the-middle and replay attacks.
- Prior to commencing the transaction, the server obtains a document from a certification authority, CA, containing:
- Server attributes such as unique and common names.
- Identity of the public encryption algorithm, Due east( ), for the server.
- The public key, k_e for the server.
- The validity interval inside which the document is valid.
- A digital signature on the above issued by the CA:
- a = S(K_CA )( ( attrs, E(k_e), interval )
- In addition, the customer volition have obtained a public verification algorithm, V( K_CA ), for the certifying authority. Today's modern browsers include these born by the browser vendor for a number of trusted certificate authorities.
- The procedure for establishing secure communications is every bit follows:
- The client, c, connects to the server, southward, and sends a random 28-byte number, n_c.
- The server replies with its own random value, n_s, along with its document of authority.
- The customer uses its verification algorithm to confirm the identity of the sender, and if all checks out, then the client generates a 46 byte random premaster secret, pms, and sends an encrypted version of it as cpms = Eastward(k_s)(pms)
- The server recovers pms as D(k_s)(cpms).
- At present both the customer and the server can compute a shared 48-byte principal secret, ms, = f( pms, n_s, n_c )
- Side by side, both client and server generate the following from ms:
- Symmetric encryption keys k_sc_crypt and k_cs_crypt for encrypting letters from the server to the client and vice-versa respectively.
- MAC generation keys k_sc_mac and k_cs_mac for generating authenticators on messages from server to customer and client to server respectively.
- To send a message to the server, the customer sends:
- c = E(k_cs_crypt)(yard, Southward(k_cs_mac) )( chiliad ) ) )
- Upon receiving c, the server recovers:
- (g,a) = D(k_cs_crypt)(c)
- and accepts it if V(k_sc_mac)(m,a) is true.
- This approach enables both the server and client to verify the authenticity of every incoming message, and to ensure that outgoing letters are only readable by the procedure that originally participated in the key generation.
- SSL is the basis of many secure protocols,including Virtual Individual Networks, VPNs, in which private data is distributed over the insecure public internet structure in an encrypted fashion that emulates a privately owned network.
15.5 User Authentication
- A lot of affiliate 14, Protection, dealt with making sure that only certain users were allowed to perform sure tasks, i.e. that a users privileges were dependent on his or her identity. Only how does 1 verify that identity to begin with?
15.5.one Passwords
- Passwords are the most mutual course of user authentication. If the user is in possession of the correct password, then they are considered to have identified themselves.
- In theory dissever passwords could be implemented for dissever activities, such as reading this file, writing that file, etc. In practice most systems apply one countersign to confirm user identity, and then potency is based upon that identification. This is a effect of the classic trade-off between security and convenience.
15.5.ii Password Vulnerabilities
- Passwords tin be guessed.
- Intelligent guessing requires knowing something about the intended target in specific, or nigh people and unremarkably used passwords in general.
- Animal-force guessing involves trying every word in the lexicon, or every valid combination of characters. For this reason good passwords should non be in any dictionary ( in whatever language ), should be reasonably lengthy, and should utilise the full range of allowable characters by including upper and lower case characters, numbers, and special symbols.
- "Shoulder surfing" involves looking over people's shoulders while they are typing in their countersign.
- Even if the lurker does not go the unabridged password, they may become enough clues to narrow it down, especially if they sentry on repeated occasions.
- Common courtesy dictates that you await away from the keyboard while someone is typing their password.
- Passwords echoed as stars or dots still give clues, because an observer can determine how many characters are in the countersign. :-(
- "Packet sniffing" involves putting a monitor on a network connection and reading data contained in those packets.
- SSH encrypts all packets, reducing the effectiveness of packet sniffing.
- However you should still never e-mail a password, particularly not with the word "password" in the same message or worse yet the subject header.
- Beware of whatsoever system that transmits passwords in clear text. ( "Give thanks you for signing up for XYZ. Your new account and password information are shown below". ) You probably want to have a spare throw-away countersign to requite these entities, instead of using the same high-security password that y'all employ for cyberbanking or other confidential uses.
- Long hard to remember passwords are oft written down, especially if they are used seldomly or must be inverse often. Hence a security merchandise-off of passwords that are easily divined versus those that go written down. :-(
- Passwords can be given away to friends or co-workers, destroying the integrity of the entire user-identification system.
- Most systems accept configurable parameters decision-making password generation and what constitutes acceptable passwords.
- They may be user chosen or machine generated.
- They may accept minimum and/or maximum length requirements.
- They may need to be inverse with a given frequency. ( In extreme cases for every session. )
- A variable length history tin prevent repeating passwords.
- More or less stringent checks can exist fabricated against password dictionaries.
xv.5.3 Encrypted Passwords
- Modernistic systems do not shop passwords in clear-text form, and hence there is no machinery to await up an existing password.
- Rather they are encrypted and stored in that form. When a user enters their countersign, that as well is encrypted, and if the encrypted version match, so user authentication passes.
- The encryption scheme was once considered safe enough that the encrypted versions were stored in the publicly readable file "/etc/passwd".
- They always encrypted to a thirteen character string, so an account could be disabled by putting a cord of any other length into the password field.
- Modern computers tin try every possible password combination in a reasonably short time, so now the encrypted passwords are stored in files that are only readable by the super user. Any password-related programs run as setuid root to get admission to these files. ( /etc/shadow )
- A random seed is included every bit office of the password generation process, and stored as part of the encrypted countersign. This ensures that if two accounts have the same plain-text countersign that they will not accept the same encrypted countersign. However cutting and pasting encrypted passwords from one account to another will give them the aforementioned patently-text passwords.
15.5.4 Erstwhile Passwords
- One-time passwords resist shoulder surfing and other attacks where an observer is able to capture a password typed in by a user.
- These are oftentimes based on a challenge and a response. Because the claiming is unlike each fourth dimension, the old response will not exist valid for hereafter challenges.
- For example, The user may be in possession of a hole-and-corner part f( x ). The system challenges with some given value for 10, and the user responds with f( x ), which the system can then verify. Since the challenger gives a unlike ( random ) x each time, the answer is constantly irresolute.
- A variation uses a map ( due east.g. a road map ) as the key. Today'due south question might be "On what corner is SEO located?", and tomorrow'due south question might be "How far is information technology from Navy Pier to Wrigley Field?" Obviously "Taylor and Morgan" would not be accustomed as a valid respond for the 2d question!
- Another option is to have some sort of electronic card with a serial of constantly changing numbers, based on the current time. The user enters the current number on the card, which will but be valid for a few seconds. A two-factor authorization also requires a traditional password in addition to the number on the card, so others may non use it if it were ever lost or stolen.
- A tertiary variation is a lawmaking book, or i-time pad. In this scheme a long list of passwords is generated, and each one is crossed off and cancelled as it is used. Obviously it is important to keep the pad secure.
fifteen.v.5 Biometrics
- Biometrics involve a physical feature of the user that is not easily forged or duplicated and not likely to be identical betwixt multiple users.
- Fingerprint scanners are getting faster, more authentic, and more economic.
- Palm readers can check thermal backdrop, finger length, etc.
- Retinal scanners examine the back of the users' eyes.
- Voiceprint analyzers distinguish particular voices.
- Difficulties may arise in the event of colds, injuries, or other physiological changes.
15.6 Implementing Security Defenses
fifteen.6.1 Security Policy
- A security policy should be well thought-out, agreed upon, and independent in a living document that everyone adheres to and is updated as needed.
- Examples of contents include how often port scans are run, countersign requirements, virus detectors, etc.
15.6.2 Vulnerability Assessment
- Periodically examine the organization to discover vulnerabilities.
- Port scanning.
- Check for bad passwords.
- Look for suid programs.
- Unauthorized programs in organization directories.
- Wrong permission bits set up.
- Plan checksums / digital signatures which have changed.
- Unexpected or subconscious network daemons.
- New entries in startup scripts, shutdown scripts, cron tables, or other system scripts or configuration files.
- New unauthorized accounts.
- The regime considers a arrangement to exist only equally secure equally its most far-reaching component. Whatsoever system connected to the Net is inherently less secure than one that is in a sealed room with no external communications.
- Some administrators abet "security through obscurity", aiming to go on as much data about their systems hidden as possible, and not announcing whatsoever security concerns they come across. Others announce security concerns from the rooftops, under the theory that the hackers are going to find out anyhow, and the simply one kept in the dark by obscurity are honest administrators who demand to get the word.
15.vi.3 Intrusion Detection
- Intrusion detection attempts to detect attacks, both successful and unsuccessful attempts. Different techniques vary along several axes:
- The fourth dimension that detection occurs, either during the set on or after the fact.
- The types of information examined to observe the attack(s). Some attacks can only be detected by analyzing multiple sources of information.
- The response to the attack, which may range from alerting an administrator to automatically stopping the assault ( e.one thousand. killing an offending process ), to tracing dorsum the attack in social club to identify the attacker.
- Some other approach is to divert the attacker to a honeypot , on a honeynet. The idea behind a honeypot is a computer running normal services, only which no 1 uses to practice whatsoever real work. Such a arrangement should non see any network traffic nether normal conditions, so any traffic going to or from such a system is by definition suspicious. Honeypots are commonly kept on a honeynet protected by a opposite firewall, which will let potential attackers in to the honeypot, just will not permit any outgoing traffic. ( And then that if the honeypot is compromised, the assailant cannot utilize information technology as a base of operations for attacking other systems. ) Honeypots are closely watched, and whatsoever suspicious activity carefully logged and investigated.
- Intrusion Detection Systems, IDSs, raise the alarm when they detect an intrusion. Intrusion Detection and Prevention Systems, IDPs, human action as filtering routers, shutting downwards suspicious traffic when it is detected.
- There are two major approaches to detecting issues:
- Signature-Based Detection scans network packets, system files, etc. looking for recognizable characteristics of known attacks, such every bit text strings for messages or the binary code for "exec /bin/sh". The problem with this is that it can only discover previously encountered problems for which the signature is known, requiring the frequent update of signature lists.
- Anomaly Detection looks for "unusual" patterns of traffic or operation, such as unusually heavy load or an unusual number of logins late at dark.
- The benefit of this approach is that it can find previously unknown attacks, so called zero-day attacks.
- Ane problem with this method is characterizing what is "normal" for a given system. Ane approach is to criterion the system, but if the aggressor is already present when the benchmarks are made, then the "unusual" activeness is recorded every bit "the norm."
- Another problem is that not all changes in system performance are the outcome of security attacks. If the system is bogged down and really slow belatedly on a Thursday nighttime, does that mean that a hacker has gotten in and is using the system to ship out SPAM, or does it merely mean that a CS 385 consignment is due on Friday? :-)
- To be constructive, anomaly detectors must have a very low false alarm ( false positive ) charge per unit, lest the warnings get ignored, as well as a depression false negative rate in which attacks are missed.
fifteen.6.4 Virus Protection
- Modern anti-virus programs are basically signature-based detection systems, which too take the ability ( in some cases ) of disinfecting the affected files and returning them back to their original status.
- Both viruses and anti-virus programs are speedily evolving. For example viruses now commonly mutate every fourth dimension they propagate, then anti-virus programs await for families of related signatures rather than specific ones.
- Some antivirus programs await for anomalies, such equally an executable programme being opened for writing ( other than by a compiler. )
- Fugitive bootleg, costless, and shared software can assistance reduce the chance of catching a virus, but even compress-wrapped official software has on occasion been infected by disgruntled manufactory workers.
- Some virus detectors will run suspicious programs in a sandbox, an isolated and secure area of the system which mimics the real arrangement.
- Rich Text Format, RTF, files cannot comport macros, and hence cannot carry Discussion macro viruses.
- Known safe programs ( e.g. correct afterward a fresh install or after a thorough examination ) can be digitally signed, and periodically the files can be re-verified confronting the stored digital signatures. ( Which should be kept secure, such as on off-line write-simply medium. )
15.6.5 Auditing, Bookkeeping, and Logging
- Auditing, accounting, and logging records tin can also be used to detect anomalous behavior.
- Some of the kinds of things that can exist logged include authentication failures and successes, logins, running of suid or sgid programs, network accesses, organisation calls, etc. In extreme cases well-nigh every keystroke and electron that moves can be logged for time to come analysis. ( Note that on the flip side, all this detailed logging tin also be used to analyze system functioning. The down side is that the logging also affects system functioning ( negatively! ), and so a Heisenberg effect applies. )
- "The Cuckoo's Egg" tells the story of how Cliff Stoll detected one of the early UNIX break ins when he noticed anomalies in the accounting records on a reckoner arrangement being used by physics researchers.
Tripwire Filesystem ( New Sidebar )
- The tripwire filesystem monitors files and directories for changes, on the supposition that most intrusions eventually result in some sort of undesired or unexpected file changes.
- The tw.config file indicates what directories are to be monitored, besides every bit what backdrop of each file are to be recorded. ( E.g. one may choose to monitor permission and content changes, but not worry about read access times. )
- When get-go run, the selected properties for all monitored files are recorded in a database. Hash codes are used to monitor file contents for changes.
- Subsequent runs report any changes to the recorded information, including hash code changes, and any newly created or missing files in the monitored directories.
- For full security information technology is necessary to also protect the tripwire system itself, most importantly the database of recorded file properties. This could be saved on some external or write-just location, only that makes it harder to change the database when legitimate changes are made.
- It is hard to monitor files that are supposed to alter, such as log files. The best tripwire can do in this case is to lookout for anomalies, such every bit a log file that shrinks in size.
- Costless and commercial versions are bachelor at http://tripwire.org and http://tripwire.com.
xv.7 Firewalling to Protect Systems and Networks
- Firewalls are devices ( or sometimes software ) that sit on the border between ii security domains and monitor/log activity between them, sometimes restricting the traffic that can pass between them based on certain criteria.
- For example a firewall router may allow HTTP: requests to pass through to a web server inside a company domain while not allowing telnet, ssh, or other traffic to pass through.
- A common architecture is to establish a de-militarized zone, DMZ, which sort of sits "betwixt" the company domain and the outside world, as shown below. Company computers can reach either the DMZ or the exterior earth, but outside computers can only accomplish the DMZ. Perchance most chiefly, the DMZ cannot achieve any of the other company computers, so even if the DMZ is breached, the assailant cannot go to the balance of the company network. ( In some cases the DMZ may accept express access to visitor computers, such equally a spider web server on the DMZ that needs to query a database on 1 of the other company computers. )
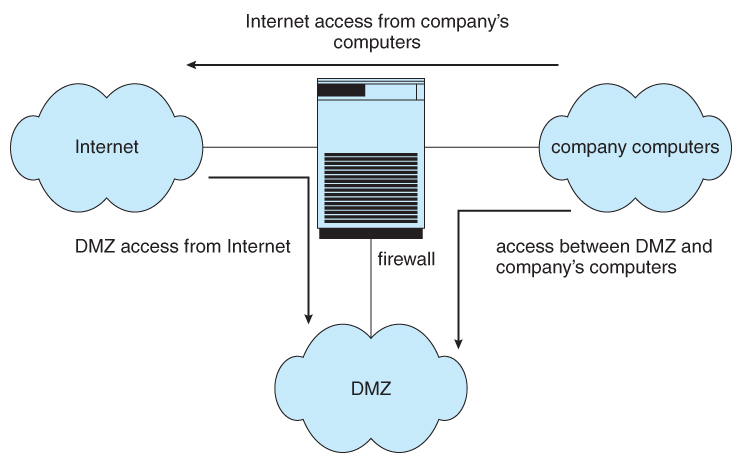
Figure 15.ten - Domain separation via firewall.
- Firewalls themselves need to be resistant to attacks, and unfortunately accept several vulnerabilities:
- Tunneling, which involves encapsulating forbidden traffic inside of packets that are allowed.
- Denial of service attacks addressed at the firewall itself.
- Spoofing, in which an unauthorized host sends packets to the firewall with the render address of an authorized host.
- In addition to the mutual firewalls protecting a company internal network from the outside world, there are as well some specialized forms of firewalls that have been recently adult:
- A personal firewall is a software layer that protects an private estimator. It may exist a part of the operating system or a separate software package.
- An application proxy firewall understands the protocols of a particular service and acts as a stand-in ( and relay ) for the particular service. For example, and SMTP proxy firewall would accept SMTP requests from the outside globe, examine them for security concerns, and forward only the "prophylactic" ones on to the real SMTP server behind the firewall.
- XML firewalls examine XML packets only, and reject ill-formed packets. Similar firewalls be for other specific protocols.
- System telephone call firewalls baby-sit the boundary between user mode and system fashion, and refuse whatever arrangement calls that violate security policies.
xv.8 Figurer-Security Classifications ( Optional )
- No computer arrangement can be 100% secure, and attempts to make information technology so tin speedily make it unusable.
- Notwithstanding one can establish a level of trust to which 1 feels "condom" using a given reckoner system for particular security needs.
- The U.S. Department of Defense'due south "Trusted Reckoner System Evaluation Criteria" defines iv broad levels of trust, and sub-levels in some cases:
- Level D is the least trustworthy, and encompasses all systems that do non run across any of the more stringent criteria. DOS and Windows 3.ane fall into level D, which has no user identification or authorization, and anyone who sits downwardly has full admission and command over the machine.
- Level C1 includes user identification and authorization, and some means of controlling what users are allowed to access what files. Information technology is designed for use by a grouping of mostly cooperating users, and describes about common UNIX systems.
- Level C2 adds individual-level control and monitoring. For example file access command can be allowed or denied on a per-individual basis, and the system administrator can monitor and log the activities of specific individuals. Another restriction is that when one user uses a system resource and then returns it back to the system, another user who uses the aforementioned resource subsequently cannot read any of the information that the outset user stored there. ( I.e. buffers, etc. are wiped out betwixt users, and are not left full of old contents. ) Some special secure versions of UNIX accept been certified for C2 security levels, such as SCO.
- Level B adds sensitivity labels on each object in the system, such as "secret", "top secret", and "confidential". Individual users have different clearance levels, which controls which objects they are able to access. All human-readable documents are labeled at both the superlative and bottom with the sensitivity level of the file.
- Level B2 extends sensitivity labels to all system resources, including devices. B2 also supports covert channels and the auditing of events that could exploit covert channels.
- B3 allows creation of admission-control lists that announce users NOT given admission to specific objects.
- Class A is the highest level of security. Architecturally information technology is the aforementioned as B3, merely it is developed using formal methods which can be used to testify that the organization meets all requirements and cannot have any possible bugs or other vulnerabilities. Systems in form A and higher may be developed by trusted personnel in secure facilities.
- These classifications determine what a organization can implement, but it is up to security policy to decide how they are implemented in practice. These systems and policies can be reviewed and certified by trusted organizations, such equally the National Estimator Security Middle. Other standards may dictate physical protections and other problems.
15.nine An Example: Windows XP ( Optional )
- Windows XP is a general purpose Os designed to support a wide variety of security features and methods. It is based on user accounts which tin can be grouped in whatsoever mode.
- When a user logs on, a security access token is issued that includes the security ID for the user, security IDs for whatsoever groups of which the user is a member, and a list of whatever special privileges the user has, such as performing backups, shutting downward the system, and irresolute the arrangement clock.
- Every procedure running on behalf of a user gets a copy of the users security token, which determines the privileges of that process running on behalf of that user.
- Authentication is normally done via passwords, merely the modular pattern of XP allows for culling authentication such as retinal scans or fingerprint readers.
- Windows XP includes born auditing that allows many common security threats to be monitored, such as successful and unsuccessful logins, logouts, attempts to write to executable files, and access to certain sensitive files.
- Security attributes of objects are described past security descriptors , which include the ID of the owner, group buying for POSIX subsystems just, a discretionary access-control listing describing exactly what permissions each user or group on the arrangement has for this particular object, and auditing control information.
- The access control lists include for each specified user or grouping either AccessAllowed or AccessDenied for the following types of actions: ReadData,WriteData, AppendData, Execute, ReadAttributes, WriteAttributes, ReadExtendedAttribute, and WriteExtendedAttribute.
- Container objects such as directories tin logically contain other objects. When a new object is created in a container or copied into a container, by default it inherits the permissions of the new container. Noncontainer objects inherit no other permissions. If the permissions of the container are inverse after, that does non affect the permissions of the contained objects.
- Although Windows XP is capable of supporting a secure system, many of the security features are not enabled past default, resulting in a fair number of security breaches on XP systems. At that place are also a large number of organization daemons and other programs that start automatically at startup, whether the system administrator has idea almost them or not. ( My system currently has 54 processes running, virtually of which I did not deliberately start and which have short ambiguous names which makes it hard to divine exactly what they practise or why. Faced with this situation, most users and administrators will simply go out alone annihilation they don't understand. )
fifteen.10 Summary
Question 13 : Which Of The Following Is Not Considered A Denial-of-service Attack?,
Source: https://www.cs.uic.edu/~jbell/CourseNotes/OperatingSystems/15_Security.html
Posted by: murrayhisclowed.blogspot.com


0 Response to "Question 13 : Which Of The Following Is Not Considered A Denial-of-service Attack?"
Post a Comment